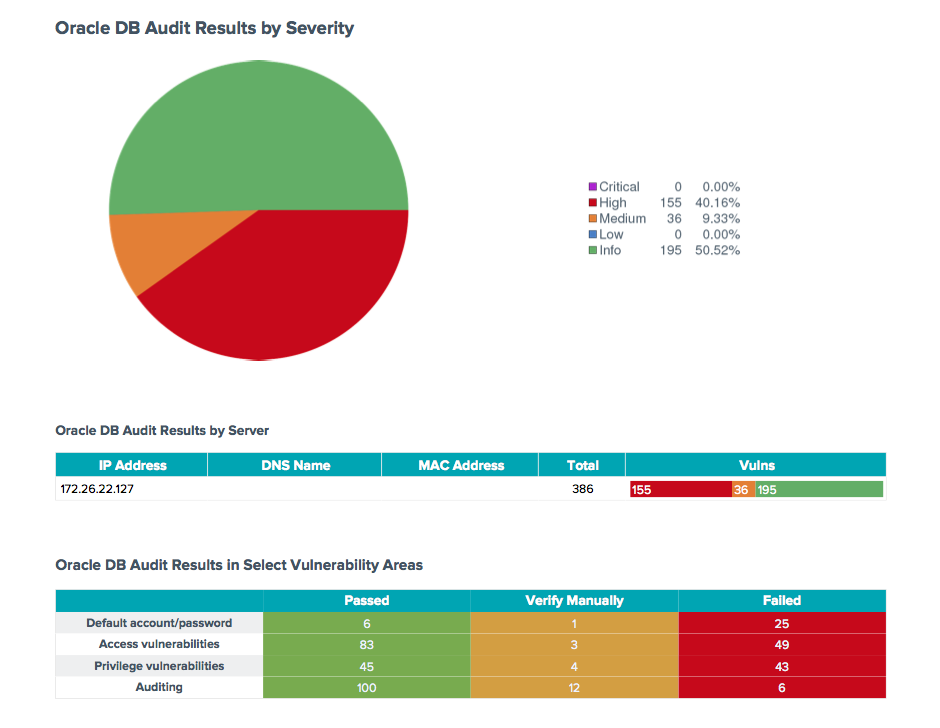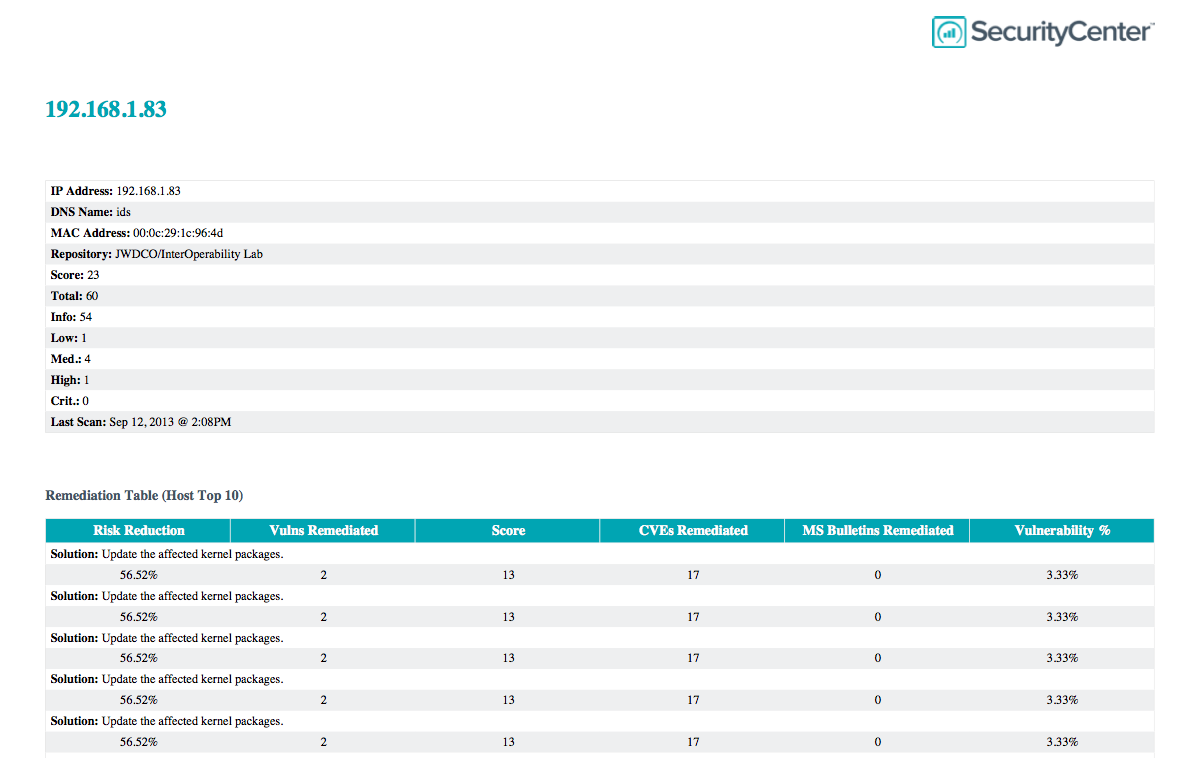
This report summarizes remediation actions across a series of hosts. Rather than just counting the number of vulnerabilities, applications are listed which need to be upgraded or patched. It also highlights systems missing one or more patches. This not only is much easier for an IT administrator to consume, it provides a measure of how much 'work' is required to secure a network, as well as the amount of risk reduced when certain patch efforts are taken.